In part 1 of this series, we configured DirectAccess for an IP-HTTPS connection in a simple (home) environment. In part 2, we enabled reporting and improved client settings to reduce connection time. In part 3, we replaced self-signed certificates by certificates generated from our PKI.
- Part 1: Implementing a Basic DirectAccess configuration with IP-HTTPS on Windows Server 2012 Core
- Part 2: Reporting and Optimizing IP-HTTPS connections
- Part 3: Authenticating IP-HTTPS connections with a PKI certificate
- Part 4: Authenticating DirectAccess clients with certificates
- Part 5: Troubleshooting guide for DirectAccess
- Part 6: Configuring DirectAccess for Windows 7
I propose to continue to improve security of our DirectAccess environment and to authenticate computer with certificates.
PART 4: AUTHENTICATING DIRECTACCESS CLIENTS WITH CERTIFICATES
1. Configure a client authentication template for auto-enrollment
On the PKI server, open the Certification Authority console
Expand your Certification Authority
Right-click Certificate Templates and select Manage
In the Certificate Templates console, right-click Workstation Authentication and select Properties
Open the Security tab
For Domain Computers, select the checkbox to Allow Autoenroll
Click on OK
Expand your Certification Authority
Right-click Certificate Templates and select Manage
In the Certificate Templates console, right-click Workstation Authentication and select Properties
Open the Security tab
For Domain Computers, select the checkbox to Allow Autoenroll
Click on OK
In the Certification Authority console tree, right-click Certificate Templates and select New > Certificate Template to Issue
Select Workstation Authentication and then click OK
Select Workstation Authentication and then click OK
Close the Certificate Templates Console.
Notes:
- You can duplicate the Workstation Authentication template and publish a custom template. However that certificate can be used for a lot of purposes: SCCM HTTPS mode.. So keep that certificate as generic as possible.
- You can limit the auto-enrollment only to the group containing the DirectAccess computer clients.
- Certain process recommend to create a custom a template and to add the Server Authentication application policy. On my own experience, that's totally useless !
2. Configure computer certificate auto-enrollment
Open the Group Policy Management Console
Expand your domain
You can create and link a specific GPO or modify an existing GPO (Default Domain Policy...)
In the console tree of the Group Policy Management Editor, open Computer Configuration\Policies\Windows Settings\Security Settings\Public Key Policies
Edit the Certificate Services Client - Auto-Enrollment policy
In Configuration Model, select Enabled
Select Renew expired certificates, update pending certificates, and remove revoked certificates and Update certificates that use certificate templates
Click OK and close the GPMC console
3. Check Client certificate
Tips:
On the Windows 8 Start Screen, simply type cert
Select Settings and click on Manage Computer certificates.
That easier than adding the certificate snap-in in a mmc console !
As soon as your computer receive GPO, "Workstation authentication" certificate is generated
4. Enable Certificate authentication for computers
Open the DirectAccess Console
In the Step 2 - Remote Access Server Box, click on Edit
Go to the Authentication step
Select Use computer certificates
Click on Browse
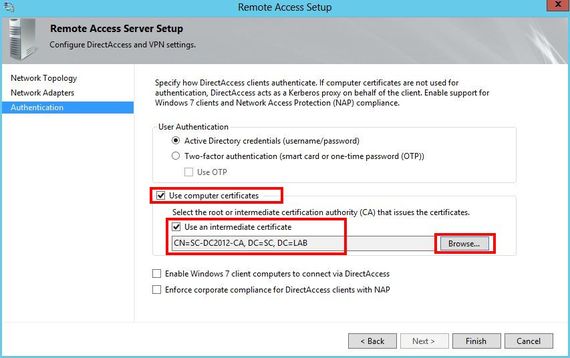
Provide the certificate of your Certificate Autority
Click on Finish
5. Logs and Authentication
Client connection is always totally transparent with DirectAccess. I propose to look at the reporting console:
Before (no certificate authentication):
After (with certificate authentication):
In the Remote Client Status console, you see for Authentication "Machine Kerberos, Machine Certificate & User Kerberos". !?!
To get more information, open the reporting console.
For the first tunnel (to reach Active Directory environment), the machine still uses kerberos authentication.
For the second tunnel, the machine uses its certificate.
You've got now a DirectAccess environment fully authenticated with certificates and that works with the IP-HTTPS protocol on a Windows 2012 core Edition.
In the next article, I will provide you some recommendations and tips from my own experience to troubleshoot DirectAccess.
See you soon
Julien













When is the Part 6 of the article be available? Thanks
RépondreSupprimerAs soon as possible. I do my best to provide the article before the end of the month. I'm quiet short of time.
RépondreSupprimerThanks for your comment!
Hi,
RépondreSupprimerThank you :-)
Found your blog superuseful...
Authentication Certificate